| | | Reduce Your Cyber Risk
A Simple Guide for Anyone | | |
|
Cyber security has, without doubt, become one of the greatest concerns affecting our everyday lives. Understanding how to lower our risk of loss from a cyber attack has become important. While there are no perfect solutions, you do not need to be an IT expert to reduce your risk significantly.
Generally cyber criminals seek ways to gain access to places where they can gain knowledge about you that could be exchanged for cash, control things you own for their benefit or take your money through theft or extortion.
To be successful cyber criminals require access to your computer system. More commonly they achieve this by taking advantage of fear or lack of thoughtfulness.
If you control access to your computer, avoid reacting in fear and take the time to think things through, you can limit the risk significantly. Here are a few things you can do:
Antivirus
The first line of defense is always a high quality anti-virus / malware prevention package with key features like automatic updates, regular automatic scanning and real time email and web browsing protection. None are perfect but having something is much better than nothing at all. This will help prevent unauthorized access to your computer. If you do not have an antivirus / malware prevention package installed on your computer, get one as soon as possible.
Email
Cyber criminals will take full advantage of this nearly uncontrollable open door to attack you. Activating your email spam filter to keep spam isolated from your regular mail will help, however, even if you have a decent spam filter, some harmful emails may still slip through.
The number one rule for reducing or avoiding risks that come through email is to assume that every email you get has the potential to be a fake, a scam or an attempt to do you harm. Until you have been able to verify an email is not fake, do not under any circumstances click on or open anything in or attached to that email.
In most instances this harm is delivered in one of or a combination of three ways.
a) A link in the email that you are asked to click on which then opens or downloads harmful programs onto your computer (a common ransom- and malware delivery tactic), or gets you to provide personal information (Phishing)
b) A file attachment which contains a harmful program. (Ransomware, malware or virus)
c) A message that is threatening, extortive or promises you some reward.
Despite the ever increasing sophistication with which these attacks are delivered, there are some tell tale signs that you could use to alert you of an attack and so avoid it. When you get an email that you are considering acting upon, it is wise to put it through a simple and rigorous question process. Being thoughtful will go a long way towards preventing loss or harm.
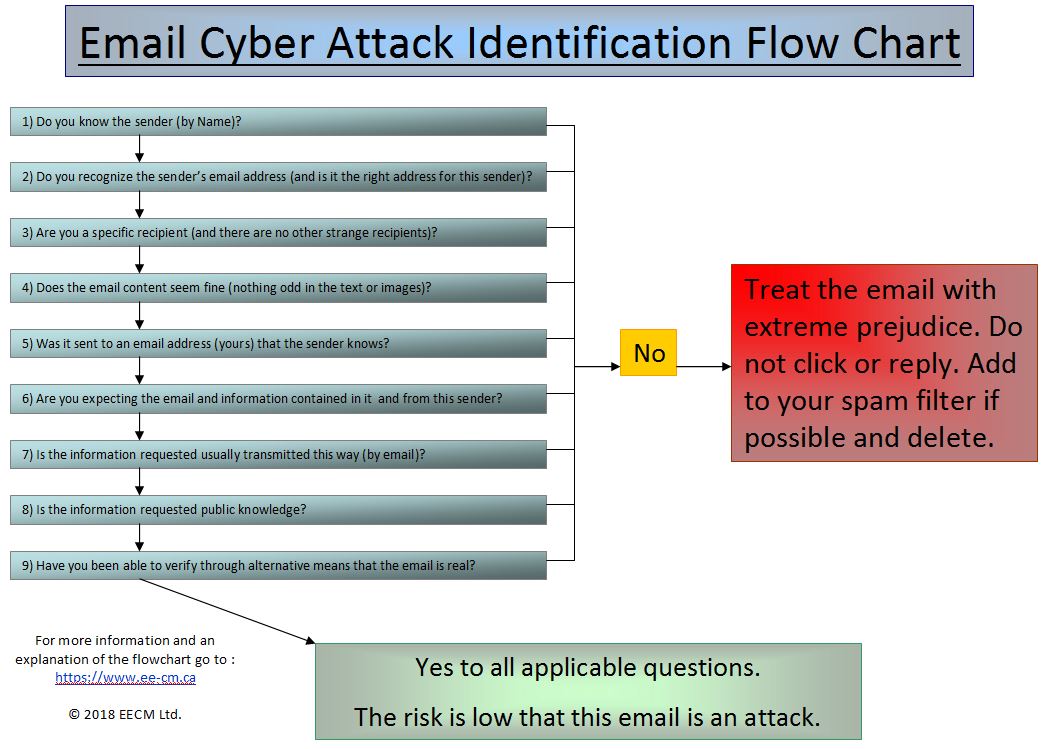
Download This Flow Chart
Explanation :
- Do you know the sender (by Name)?
If the answer is no it is most likely spam, even if not harmful. If the answer is yes, this does not mean it actually came from that person. Further checking may be in order.
- Do you recognize the sender's email address (and is it the right address for this sender)?
Does the email address match the one you have on record for this sender or is it some odd unknown email address? Even if the sender's name is correct, if the email address is not the right one, it is probably an attack or at the very least spam. Make sure to check the underlying email address. This can be done, depending on your email program, by double clicking on the sender or by hitting the "Reply" button without sending.
- Are you a specific recipient (and there are no other strange recipients)?
Is this email specifically addressed to you by name? Less sophisticated cyber criminals may send emails in bulk by copying several addresses, most of which will be unfamiliar or strange, in the "TO" or "CC" field of an email. They may also use the "BCC" function, in which case you may not be an actual recipient listed. Though this is not a certain sign that it is an attack or spam, it should raise at least some further questions.
- Does the email content seem fine (nothing odd in the text or images)?
Miss-spelt names, weird and out of place text like "Dear <name>" instead of your actual name are often signs of bulk emails. Cyber criminals use little programs to send their email so they can send thousands of emails in bulk quickly. These programs are designed to automatically populate recipient specific information into email content from databases. If they do not have correct information or their program does not work properly this will often show up in weird text or images in the email content.
- Was it sent to an email address (yours) that the sender knows?
One of the most potent forms of attack involves impersonation of someone you know. If you have more than one email address (e.g. one for work and one private) and you receive a work related email on your private account, be very careful. This is probably an attack. Another example is if you use your personal email address for personal banking and you get an email from your bank on your work email address. This is a red flag for sure.
- Are you expecting the email and information contained in it and from this sender?
This is where thoughtfulness and working with fear comes into play in a big way. If you get an email from someone, like your bank, asking you to do something, did you expect the email? If not be careful about acting on it. Also does the question come from someone familiar at the bank?
Often cyber criminals will send emails promising you money or a discount if you click on something. Small discount offers are probably more hazardous than promises of untold riches because they are more believable. (E.g. $50 from Amazon). Beside the obvious "you have won a lotto you have never entered" or "inherited from some remote person unknown to you" ask yourself if the company sending the "offer" would really bother with you. Chances are not.
If you are not expecting it, do not be tempted to click on it. If you are unsure if "Amazon" has sent you a discount voucher do not click on the link (or attachment) in the email. Instead log into your "Amazon" account using a link that you know and have checked. If it is real, the offer will appear there. If not. Ignore the email completely.
A too simple message from someone you know like "Hi I thought you would love this article" or "check this out", with a link, is potentially an attack.
No one expects to be threatened and any threats do inspire fear. Some of the most potent extortion emails involve threats from creditors (you have never heard of) or threats from lawyers, police, tax agencies and even banks. Ask yourself if these agencies would typically communicate through email that you have "an arrest warrant outstanding" or "owe them money". Tax agencies, police and banks do not make a habit of communicating such things through email. They will call you or send someone to your house for a start.
If you get a threat from anyone attempting to extort you for any reason whatsoever especially with a request for payment to a crypto currency account, treat it with extreme prejudice. Ignore, add to spam filter and delete.
One of the latest extortion scams doing the rounds is a threat of exposing your porn habits. These emails often include a familiar password you have used at some point as a way of establishing their credibility. If the password is familiar, just change the password on anything you have used it for and ignore the threatening email. If you have concern that the threat is real, contact your local police immediately.
- Is the information requested usually transmitted this way (by email)?
This is very often a sign that something is not right. You are asked to transmit information to your bank or government agency that is not usually transmitted through email. Be very careful with these. Only respond if you have independently verified that this email is real.
- Is the information requested public knowledge?
Don't assume that low risk information is useless to cyber criminals. As a matter of course you should not, under any circumstances, send any sensitive or private information by email or enter it by clicking on a link provided in an email, unless you have independently verified that it is a legitimate request.
For example, if your bank needs you to send information and you are uncertain about the email, call them. Check if it is a real request. The same for requests from tax or government agencies. Unless you are expecting the request from a specific lawyer, ignore it. It is an attack.
- Have you been able to verify through alternative means that the email is real?
If an email is attempting to secure sensitive information, is soliciting you to click on a link or contains any attachments, knowing with certainty that an email came from someone you know and is an email you are expecting is without a doubt the safest way to avoid an email style cyber attack. If you are unsure rather verify. Call or verify by some other means.
Remember that anything that is really important enough to be pursued will likely be pursued by means other than just through your email. And if someone actually needs something from you, you can be sure they will bug you again and probably through some other means.
Browsing the internet
Browsing the internet comes with some risks for the same reasons as with email. There are many websites that are purely designed to cause you harm and often appear completely innocent. Also sites that are not intending to cause harm are sometimes altered by those wanting to cause harm. Fortunately if you have a decent antivirus / malware package with real time browser scanning / web protection you can mostly eliminate these risks.
In addition you can also follow a few extra precautions, including :
- Do not enter private information on websites that are not displaying a little padlock in the browser URL bar. (These sites are not encrypted.)
- Be wary of strange or unfamiliar URLs (addresses for the websites), especially when entering your personal information (especially credit card information). Cyber Criminal are often very successful at impersonating legitimate websites. If you are doing banking or doing something else important, make sure that the URL is independently verified as the correct one. If you are unsure call the bank and get the right URL.
- Open any important website (like your banking) in a new browser window. NOT in a new tab. It is possible for open sites to access information across tabs in the same window.
- Be especially careful of websites that distribute things like adult content. Being curious or even accidentally opening an adult site can cause a lot of grief.
- Use only passwords that comply with the following minimum requirements :
- Use a unique password for everything.
If you use the same password for multiple sites, access is essentially open to all those the moment one password is discovered.
- Use strong passwords.
Unfortunately password strength is important. Do not use numbers or letters that are typical to your identity and easily gotten from other sources like your date of birth, your initials or your dog's name. This is a pain but the less connected your passwords are to your identity, the less likely they are to be discovered by criminals.
Use different combinations of numbers, letters and special characters and the longer your password the better. It does make it considerably more difficult to guess or use special programs to crack. Getting a replacement password is usually not too difficult either so concern about forgetting should not be an obstacle for you to use strong passwords. If you have trouble with remembering your passwords, an option is to keep the names and your current passwords for sites in a hand written notebook.
- Change your passwords regularly.
The more often you change your important passwords the less likely it is that someone will gain unauthorized access. Recommended is every 30 days but for most things every 90 days will suffice.
- If it is an option, use a specific credit card with a low limit for any of your internet purchases. Having a completely separate credit card, not connected to you regular bank for internet purchases will reduce the level of exposure that you have in case someone nefarious does get a hold of your credit card information through a website.
In conclusion
In a world that is increasingly driven by cyber space, one can easily become a victim of this crime and all its resulting difficulties. Being aware of your risk and then taking at least some of the simple steps highlighted in this article should help to reduce your risk to a point where interacting with cyber space does not require your own personal IT protection squad. Be thoughtful and trust yourself. If something does not feel right, err on the side of caution.
Author : Pieter Heydenrych CIP
© 2018 EECM Ltd. https://www.ee-cm.ca
|
|
| |
| |